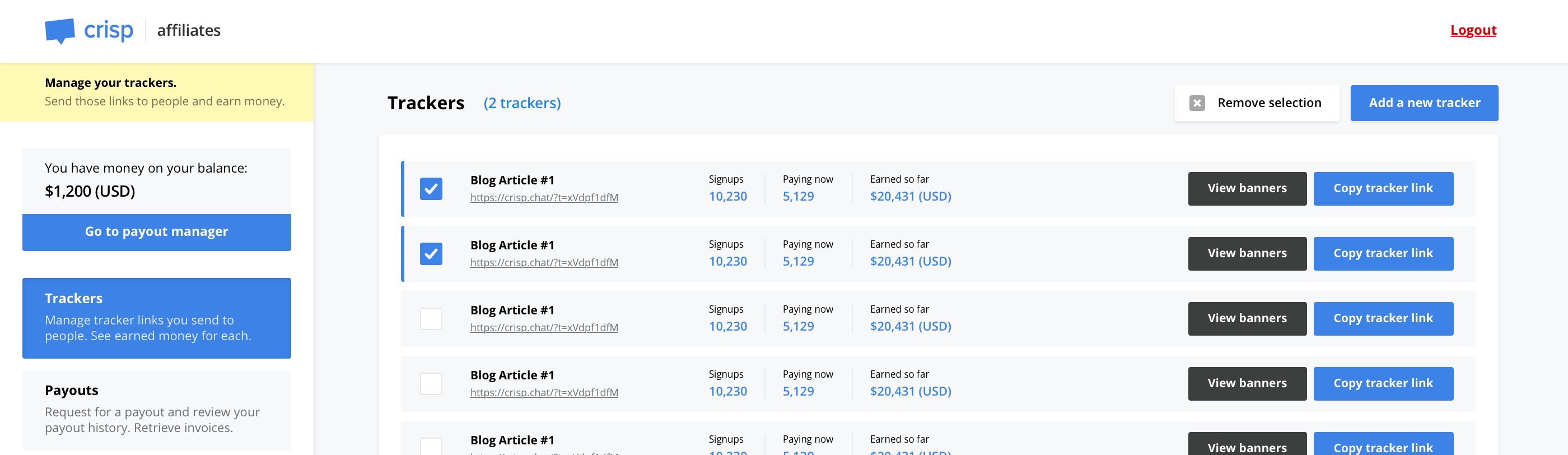
Affiliates dashboard. Used by affiliates to generate tracking codes and review their balance.
Raider is easy to integrate in your existing system. You can also customize the dashboard look & feel with templates and styles. It can be used as a self-service affiliates system, for your affiliate users to manage their account, create tracking URLs, review their balance and request for payouts.
| Crisp |
👋 You use Raider and you want to be listed there? Contact me.
Raider provides a self-service affiliates dashboard on which users can sign up, login, and manage their account (eg. create tracking codes, request for payouts, etc.). Your backend can report referred customer payments to Raider, so that the affiliates can cash out their commission and request for a payout at any point.
Raider provides two services:
Install from releases:
The best way to install Raider is to pull the latest release from the Raider releases page.
Make sure to pick the correct server architecture (eg. Intel 32 bits).
Install from Cargo:
If you prefer managing raider via Rust's Cargo, install it directly via cargo install:
bash
cargo install raider-server
Ensure that your $PATH is properly configured to source the Crates binaries, and then run Raider using the raider command.
Install from sources:
The last option is to pull the source code from Git and compile Raider via cargo:
bash
cargo build --release
You can find the built binaries in the ./target/release directory.
Install the libssl-dev (ie. OpenSSL headers) before you compile Raider. SSL dependencies are required for email notifications.
Raider requires a MySQL to be running on your host (it is unfortunately not compatible with PostgreSQL and others, at the moment).
The Raider SQL schema should be imported in the Raider database you created, which you can find at raider.sql.
Use the sample config.cfg configuration file and adjust it to your own environment.
⚠️ Important: Make sure to change the default server.secret_key configuration value with a secret key you generated. Also, generate a random arbitrary length string for database.password_salt. Failing to change any of those values will make your Raider instance insecure.
Available configuration options are commented below, with allowed values:
[server]
log_level (type: string, allowed: debug, info, warn, error, default: warn) — Verbosity of logging, set it to error in productioninet (type: string, allowed: IPv4 / IPv6 + port, default: [::1]:8080) — Host and TCP port the Raider service should listen onworkers (type: integer, allowed: any number, default: 4) — Number of workers for the Raider service to run ontrack_token (type: string, allowed: secret token, default: no default) — Track API secret token (ie. secret password)secret_key (type: string, allowed: 192-bit base64 encoded secret key, default: no default) — Secret key for cookie encryption (see Rocket docs for details)[database]
url (type: string, allowed: MySQL URL, no default) — URL of the MySQL database to connect topool_size (type: integer, allowed: any number, default: 4) — Number of connections to maintain to MySQLidle_timeout (type: integer, allowed: seconds, default: 300) — Idle timeout in seconds to MySQLconnection_timeout (type: integer, allowed: seconds, default: 10) — Connection timeout in seconds to MySQLpassword_salt (type: string, allowed: any string, no default) — Password salt (preferably strong and long; do not change this after accounts got created as it will make them unusable)[email]
from (type: string, allowed: email address, no default) — Email address from which to send emailssmtp_host (type: string, allowed: hostname, IPv4, IPv6, default: localhost) — SMTP host to connect tosmtp_port (type: integer, allowed: TCP port, default: 587) — SMTP TCP port to connect tosmtp_username (type: string, allowed: any string, no default) — SMTP username to use for authentication (if any)smtp_password (type: string, allowed: any string, no default) — SMTP password to use for authentication (if any)smtp_encrypt (type: boolean, allowed: true, false, default: true) — Whether to encrypt SMTP connection with STARTTLS or not[assets]
path (type: string, allowed: UNIX path, default: ./res/assets/) — Path to Raider assets directory[branding]
page_title (type: string, allowed: any string, default: Affiliates) — Affiliates system titlepage_url (type: string, allowed: URL, no default) — Affiliates system URLhelp_url (type: string, allowed: URL, no default) — Help URL to be used in dashboard (ie. knowledge base where users can search for help)support_url (type: string, allowed: URL, no default) — Support URL to be used in dashboard (ie. where users can contact you if something is wrong)icon_color (type: string, allowed: hexadecimal color code, no default) — Icon color (ie. your icon background color)icon_url (type: string, allowed: URL, no default) — Icon URL, the icon should be your squared logo, used as favicon (PNG format recommended)logo_white_url (type: string, allowed: URL, no default) — Logo URL, the logo should be your full-width logo, used as login, signup & account recover form logo (whiter logo, SVG format recommended)logo_dark_url (type: string, allowed: URL, no default) — Logo URL, the logo should be your full-width logo, used as dashboard header logo (darker logo, SVG format recommended)custom_html (type: string, allowed: HTML, default: empty) — Custom HTML to include in affiliates system head (optional)[tracker]
track_url (type: string, allowed: tracker URL, no default) — Tracker URL, to which tracker links will point totrack_parameter (type: string, allowed: tracker query parameter, default: t) — Tracker query parameter used in URL (eg. ?t=xDJSas10)commission_default (type: float, allowed: percentage from 0.00 to 1.00, default: 0.20) — Default commission percentage (for new accounts)[[tracker.banner]]
banner_url (type: string, allowed: image URL, no default) — URL to the banner imagesize_width (type: integer, allowed: image size in pixels, no default) — Width of the banner (in pixels)size_height (type: integer, allowed: image size in pixels, no default) — Height of the banner (in pixels)[payout]
currency (type: string, allowed: currency code, default: USD) — Currency to be used for payouts (and balances in general)administrator_email (type: string, allowed: email address, no default) — Email address of the affiliates system administrator (payout request emails will be sent there)Raider can be run as such:
./raider -c /path/to/config.cfg
When a payment for which you have a tracking_id is made on your platform (ie. a payment for a customer that was referred by an affiliate); your backend needs to submit this payment to the Raider tracking API. The full payment amount needs to be submitted, as the commission percentage is applied by Raider itself.
👉 Cannot find the library for your programming language? Build your own and be referenced here! (contact me)
In case you need to manually report tracked payments to the Raider endpoint, use the following HTTP configuration (adjust it to yours):
Endpoint URL:
HTTP POST https://affiliates.example.com/track/payment/<tracking_id>/
Where:
tracking_id: The tracking identifier associated to customer who paidRequest headers:
Authorization header with a Basic authentication where the password is your configured server.track_token.Request data:
Adjust the request data to your payment context and send it as HTTP POST:
json
{
"amount": 95.00,
"currency": "USD",
"trace": "Plan: Unlimited; Customer: valerian@crisp.chat; Website: crisp.chat"
}
Where:
amount: The full amount of the payment (Raider process the commission amount itself, eg. with 20% commission you send 100.00 and Raider processes it as 20.00)currency: The payment currency code (if the currency is different than the default currency configured with payout.currency, a conversion is applied using current day market rates)trace: An optional trace value which is logged in the database (may be used for your own records; this is never visible to your affiliate users)In case you need to manually report tracked signups to the Raider endpoint, use the following HTTP configuration (adjust it to yours):
Endpoint URL:
HTTP POST https://affiliates.example.com/track/signup/<tracking_id>/
Where:
tracking_id: The tracking identifier associated to customer who signed upRequest headers:
Authorization header with a Basic authentication where the password is your configured server.track_token.If you find a vulnerability in Raider, you are more than welcome to report it directly to @valeriansaliou by sending an encrypted email to valerian@valeriansaliou.name. Do not report vulnerabilities in public GitHub issues, as they may be exploited by malicious people to target production servers running an unpatched Raider server.
:warning: You must encrypt your email using @valeriansaliou GPG public key: :key:valeriansaliou.gpg.pub.asc.
:gift: Based on the severity of the vulnerability, I may offer a $100 (US) bounty to whomever reported it.